Information Sheets
This information sheet is intended to assist Commonwealth officials at the Specialist and Senior Executive Officer level understand:
- The benefits of engaging and seeking the advice of independent advisors to inform the management of risk,
- The role of engaging an independent advisor,
- When entities should consider engaging an independent advisor,
- How agencies would go about seeking the views of an independent advisor,
- Practical examples of agencies successfully leveraging the skills of an independent advisor to better inform their management of risk,
- The process of evaluating the role of an independent advisor and assessing their effectiveness.
An external party can help uncover and harness any potential opportunities or new directions that are associated with the better practice of risk management. Their independent perspective and experience with successful strategies in other organisations can offer insight into the effectiveness of an entity’s processes. This might include areas such as an entity’s structure of governance, operating model, risk management policy and supporting processes, risk culture, risk assessment, risk mitigation, risk capability, control performance, risk training, risk systems, risk escalation and reporting. This provides an opportunity to streamline procedures and challenge the assumptions and perceptions embedded across an entity, preventing any potential groupthink. In this way, an entity can strengthen their ‘third-line (of defence)’ by seeking insights from an objective independent.
Targeted assistance
Advisors can be targeted as subject matter experts to leverage their ideas, experience, schools of thought or objective input to assist in addressing a specific or broader risk profile. Developing a trusted partnership with this adviser can facilitate frank and fearless conversations about risk and offer fresh perspectives.
Identifying blind spots
Without external and objective support, entities can potentially overlook prominent factors or issues in relation to their operating environment. In this way, an independent advisor and a fresh set of eyes can help critically analyse the environment, mindset and decision-making process that affects the risk management approach within an entity. These advisors can observe, review and critique the risk culture and provide advice on improvements to the entity’s identification, escalation and management of risk. This approach can help usher in change and broaden the horizons of how an entity views a particular issue or risk.
Expanding your network
A good independent advisor will draw threads between risk issues that are common across multiple entities through their wealth of experience and assist in engaging with external or internal stakeholders. This will open avenues of communication to networks that the entity would otherwise not have access to.
Realising opportunities
Independent advisors can challenge a risk adverse mindset and encourage the entity to positively engage with risk, if it aligns with their risk appetite. When supporting an Audit Committee or an Executive Leadership Team, independent advisors can encourage the connection of risk management with the strategic and business planning process of an entity, as opposed to the traditional alignment with the compliance aspect of business. If they are effectively engage, these advisors can add to the credibility of the operation of an entity’s Audit and Risk Committee.
An independent advisor can be a risk subject matter expert, specialist or observer who can share their experience and insight with an entity, project or team to enhance their capabilities and operations. They can be from within an entity’s portfolio, another government entity or can be external. The key is that they bring a level of expertise not readily available or offer insight on particular areas of risk that are a cause for concern.
An independent advisor can potentially be a candidate who has been a member of multiple entity audit and risk committees or had experience of sitting on a variety of boards across the commonwealth or within industry. Their skillset does not have to be specifically related to risk management and their engagement does not necessarily need to come at a cost to an entity.
These advisors can work on a longer-term basis and could potentially assume leadership roles within an entity’s risk committee. Alternatively, they could take up a consultant role and work on a shorter-term basis. Here, they could be hired to address a very specific problem affecting an entity, or even provide advice and expertise in relation to a new business venture.
Independent advisors can be used to help an entity shape and achieve their overarching strategic objectives through the better consideration and management of risk. They can be leveraged to help encourage risk information to be used in all decision-making across the agency.
There are no set parameters and specific requirements that an independent advisor should meet. The entity should assess where their existing needs and capability gaps lie in relation to current roles and responsibilities and engage an independent advisor accordingly.
There are a number of ways in which an independent advisor can be engaged:
- Across the government there are a number of management advisory service panels available that could operate as mechanisms and ways in which entities are able to use independent advisors
- Communities of practice can be leveraged to help identify a potential subject matter expert
- A mutual cooperation or support system between other entities outside of or within their portfolio can be established. Advisory services can be exchanged whereby a member of each entity can serve a period on the other’s audit and committee boards or as an observer to share experiences and insights into best practice risk management
- Drawing from the experience and expertise of former senior APS executive officers. Research can be undertaken into relevant reviews and pieces of work that relate to your own area of concern or business need, allowing entities to discover and reach out to subject matter experts or external advisors that could provide assistance in achieving targeted business outcome
- Engaging an advisor in the course of the entity adopting a lessons learned approach at the conclusion of the project in order to assess and identify any improvement opportunities.
During the engagement of the independent advisor, entities may look to assess the effectiveness of their output and ability to help inform the management of risk through the following processes:
- KPIs can be embedded into a contract, terms of reference for an entity risk committee, MoU, letter of engagement in order to be able to readily measure an independent advisor’s value and contribution to an entity
- A lessons-learned analysis can be undertaken that looks into evaluating the performance of an independent advisor. This can be used as a tool to reflect on the use of the advisor and their ability to enhance the entity’s engagement with risk, in order to ensure that an independent advisor can be used more effectively going forward.
- Where an independent advisor’s engagement is ongoing, entities may undertake a periodic assessment of the performance of this type of advisor in conjunction with reviewing the effectives of the audit and/or risk committee. This assessment could inform the agency as to whether there is a need for similar advisors to be engaged in the future.
However, these types of advisor roles may inherently offer an intangible and unmeasurable benefit to the entity that broadens the horizons of the risk management discourse and challenges the thought processes within an entity.
This information sheet is intended to assist Commonwealth officials at the Specialist level understand:
- what Key Risk Indicators (KRIs) are and their benefits,
- types of KRIs and reporting on them, and
- practical tips on developing KRIs.
Key Risk Indicators (KRIs) are measures and metrics that relate to a specific risk and demonstrate a change in the likelihood or consequence of the risk occurring.
KRIs provide an early warning to identify potential events that may harm continuity of an activity/project.
There are a number of benefits to identifying and using KRIs. They:
- add more detail and information to risk assessments, making them more reliable and informative to management,
- allow for proactive identification of emerging risks by creating an informative framework in which to scan for what is on the horizon,
- detail at what level a risk is considered important for attention or for direct intervention, and
- can help management track trends in risks to the entity.
Types of KRIs
Lagging - monitor data retrospectively to identify changes in the pattern or trend of risk/activities. These types of KRIs ensure that the exposure is minimised as soon as practicable to prevent or reduce further exposure or consequence.
Leading / predictive - are used to signal changes in the likelihood of a risk event. These types of KRIs are more likely to aid management in taking action in advance of risks materialising.

|
|
|
|
The determination of effective KRIs starts with an understanding of the entity’s purpose and objectives. An effective set of KRI metrics will provide insight into potential risks that may impact the realisation of objectives or may indicate the presence of new opportunities.
The below diagram illustrates the identification of 4 key objectives aligned to the entity purpose. Linked to the objectives are several potential critical risks that may impact on one or more of the objectives. KRIs have been mapped to each critical risk to reduce the likelihood of the risks occurring and to provide insight and information to senior management of any risks that could potentially hinder the achievement of the entity objectives and strategy.
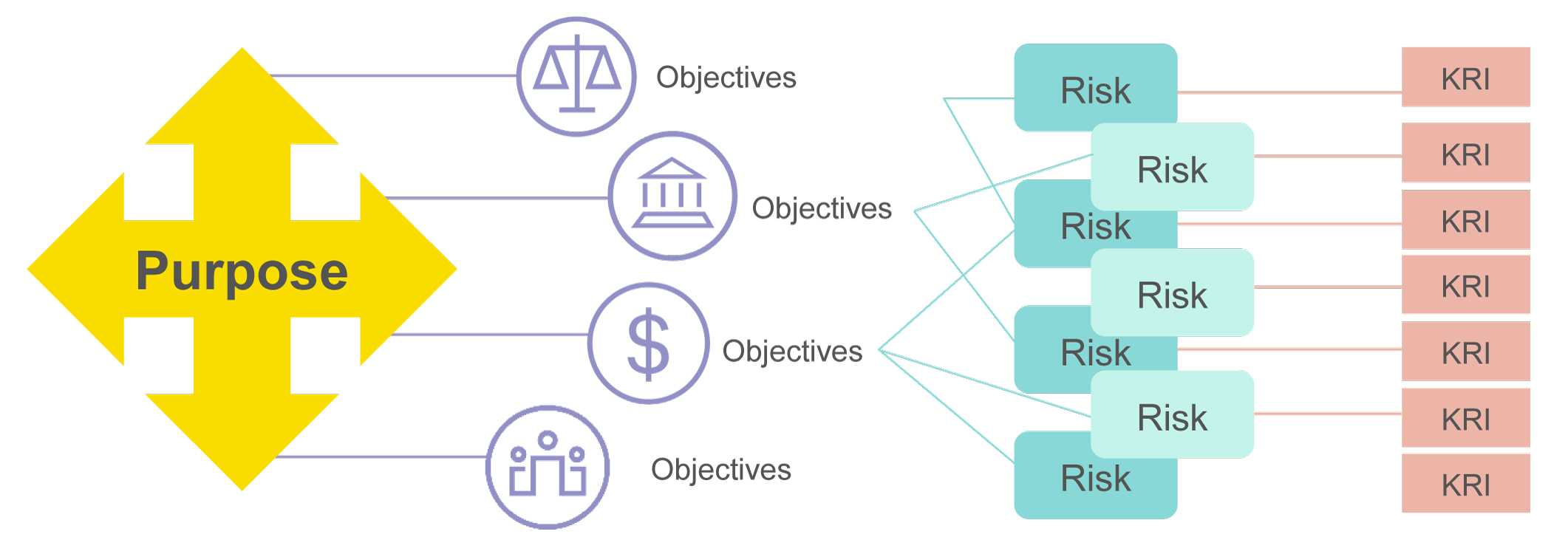
KRIs are most effective when they are:
- Measurable – are the metrics quantifiable e.g. number of, percentage
- Trackable – allowing comparisons to be made over time to provide trending
- Predictable – provide warning signs of potential risk events
- Informative – measure the status of the risk.
KRI thresholds
Prior to monitoring KRIs, levels of threshold should be determined by management that will trigger action. This creates a more pro-active approach to the management of risk through the identification of actions that will reduce the likelihood of a risk event occurring and/or limit risk exposure to within risk appetite tolerances.
KRI thresholds should be reviewed often to ensure they are set so the lower and upper triggers capture events or trends that serve as predictive indicators. The thresholds should not contradict the “risk appetite” of the entity.
When determining the thresholds and trigger points for KRIs, consider the following:
- Risk appetite and tolerance.
- Is there any historical data available on the KRI?
- When does management want to intervene to ensure adequate action and mitigations are put in place?
| KRI | Green | Amber | Red |
|---|---|---|---|
| # of key persons voluntary resignations (key person are those identified as successors to senior roles) | <1 per quarter | 1 – 3 per quarter | >3 per quarter |
In the above example, data would be available from HR systems and action should be taken at the amber trigger to understand reason for leaving, this could be done via methods such as exit interviews, looking at staff engagement survey results or one on one meetings with key persons.
Using past events to identify leading indicators
Reviewing a “risk event” that has affected your entity in the past is a great way to determine leading indicators that could assist in identifying a similar emerging risk from happening again.
Consider the root causes of the past event, speak to subject matter experts who managed and implemented actions to minimise the consequence of that risk and understand the availability of data that could be used to reduce the likelihood of that risk event reoccurring. The closer the KRI is to the root cause of the risk event, the more likely the KRI will trigger pro-active management and action.
Reporting of KRIs can assist in alerting management to trends that may adversely affect the achievement of entity objectives. They can identify current “risk exposure” and “emerging risk” trends. The frequency of data collection and reporting of KRIs should be agreed and communicated to all staff who play a role in sourcing, collating and reporting on the data. When reporting on KRIs, consider the following:
Availability of data
- What data should you be looking for?
- What data is currently being captured that could be used to measure KRIs?
- What historical data is available to indicate trending when first establishing a set of KRIs?
- How often is data captured and available for reporting purposes?
Data sources
- What data sources are available?
- Have you identified and met with the teams who manage the data sources?
- Communicate with those who manage the data sources to determine the frequency of when data is available and the importance of gathering information within an agreed period of time
- What is the degree of automation for the data source – i.e. manual v interface? (automated data is more reliable and should be used in the first instance to ensure accuracy of reporting)
- Often risks likely to have a significant consequence arise from external sources such as economic downturns, legislation changes or interest rate shifts. Think about what external sources of data are available to assist in identifying emerging risks to your entity, for example published unemployment rates.
Data integrity
- The quality and integrity of data will provide an accurate view of current KRI trending to enable effective management of risks.
- How reliable is the available data?
- Is the available data complete, current and concise?
- Is there any requirement for standardisation or tailoring of data? Trending and/or aggregation may lose integrity if standardisation and tailoring of information is required and performed by multiple users.
Reporting of KRIs is beneficial to risk owners, risk managers, senior managers and often Board members and could be included in “risk reporting” to inform and provide oversight of the management of risk.
It is recommended to report KRIs on a dashboard that will easily highlight the outcome of the KRI and the trending data. The simple use of colour will alert management to areas where attention is required. It is important to remember that KRIs do not manage or treat risk, and could lead to a false sense of security if poorly designed.
An example of a KRI dashboard
Some examples of KRIs and what they could be telling us:
Number of key persons voluntary resignations (key person are those identified as successors to senior roles).
- This KRI could be used as an indicator for human resource/people risks. It could alert management to:
- Poor succession planning
- Lack of information/knowledge sharing
- Key person risk
- Poor management
- Poor staff engagement
- Lack of incentives, rewards or recognition.
Percentage of incidents where customer personal data is put at risk
- This KRI can be used as an indicator for legal/compliance risks, technology risks, fraud risks, reputational risks. It could alert management to:
- Poor technology/cyber risk controls
- Lack of adherence to policy or processes
- Failure to meet compliance obligations
- Potential scrutiny from regulators or media which will impact the reputation of the entity.
Percentage of disaster recovery plans tested in the past 12 months
- This KRI can be used as an indicator for Business Continuity or technology risks. It can alert management to:
- The possibility of system failures
- Poor business continuity planning or business impact analysis
- Slow recovery times
- Retention of data.
- Limit the number of KRIs and focus on high/critical risks. While there may be many KRIs that could be linked to a risk, selecting 2 -3 of the more impactful and informative KRIs will provide more rigour in your risk assessment
- When identifying data sources, do not limit them to internal sources only. External data sources could highlight new or emerging risks which could impact your business
- It is better practice to have automated data for KRIs to avoid manual manipulation of data and the risk of human error
- Think about whether the KRIs you identify may be used to incentivise or motivate your staff, for example, are there any KRIs that can be linked to performance scorecards?
- KRIs can serve as an input to determine a realistic risk appetite. The monitoring of KRIs is an important mechanism by which an entity’s management can gain assurance that it remains within its stated appetite for operational risk
- Review thresholds and trigger points overtime to ensure they stay aligned with the risk appetite of the entity
- Identified KRIs should inform trending over time. Trending can alert management to a deterioration in risk management and adequate action can be put in place
- Present KRIs in a dashboard format, the simple use of colour provides a quick visual to management and can highlight focus areas
Remember that KRIs do not treat or manage risks, they are indicators that demonstrate a change in the likelihood or consequence of the risk occurring.
This information sheet is intended to assist Commonwealth officials at the Specialist level understand:
- what a risk profile is and how they can be presented,
- how a risk profile can be used to support decision making, and
- practical steps for developing, maintaining and reviewing a risk profile.
A risk profile is a description of any set of risks. The set of risks can contain those that relate to the whole entity, part of the entity or as otherwise defined.
An entity’s risk profile can contain risks of different natures. Some of these may be managed at an enterprise level and represent the most significant risks exposures of the entity, others will be managed within business units and represent more focused concerns.
Risk profiles can be represented in different ways and can be used to highlight different messages to different audiences.
Examples of some of the issues a risk profile can communicate include:
- The overall level of risk being carried by the entity.
- How the entity’s current risk exposure compares to its appetite for risk.
- Themes, patterns or common issues amongst the entity’s risks.
- Areas of shared risk or interdependency.
- Warning of emerging or worsening risk exposures.
- Detail on the nature of individual risks.
The underlying data for an entity’s risk profile is commonly contained in one or more risk registers. Typically, each risk register contains information in a spreadsheet or database format. For each risk, this might include the risk event, its category, the inherent risk rating, sources or causal factors, links to risks in other registers, controls and control effectiveness rating, and residual risk rating. Each entity will present this differently though in a format that suits them. An illustrative example of a simple risk register is provided at Appendix A.
As a typical risk register contains a lot of detail, it is not always the best way of presenting risk information to senior decision makers. A risk profile can be an effective way of summarising the information held in the entity’s risk registers in an easy to understand format.
Consider the audience and their information needs when portraying the risk profile. Four examples of different risk profile representations are provided at Appendix A. They include a simple risk register format, a ‘heat map’ or risk severity matrix, a graph of inherent risk against the effectiveness of current controls, and a comparison of risk severity against risk tolerance.
Ultimately, the accountable authority is responsible for ensuring the appropriate management of an entity’s risk profile. In practice, the manager/s of the entity’s risk registers, and therefore the profile, will vary depending on the size, nature and complexity of the entity. The table below highlights how risk profile maintenance can be devolved, centralised or managed in a hybrid model.

Better informed decision making and corporate planning
A key purpose of a risk profile is to support effective decision making in circumstances of uncertainty.
By clearly highlighting where key risk exposures exist, senior decision makers can work to manage these and avoid action which would drive the risk outside of acceptable tolerances.
Improved ability to anticipate change, emerging risk and disruption to operations
A risk profile can support the consideration of emerging and future risk as well as current exposures so that contingency plans can be developed where required.
A disciplined approach to risk profile maintenance includes an ongoing process to identify new or emerging risks and analyse the threats and opportunities they may represent. This process helps the entity to:
- understand the likely effectiveness of existing strategies and controls in mitigating emerging risk and optimising opportunity,
- understand how new risk changes the overall exposure of the entity,
- understand the impact that the changed risk profile could have on stakeholders and shared risks, and
- anticipate change and disruption to operations.
Understanding risk exposure compared to risk appetite
A good representation of an entity’s risk profile will support senior officials to understand whether the entity is holding too much, too little, or just enough risk.
Where an entity has a well-defined risk appetite, this can be represented within the risk profile. The risk profile can be used to clearly highlight where activities, programs or business units are operating outside defined risk tolerance thresholds.
The following is one approach to developing, analysing, maintaining and communicating a risk profile. The actual process used may be tailored to the specific needs of each entity or circumstance.

A first step is to develop the risk profile by conducting a risk assessment and capture the outcome in a risk register. Depending on the size of the entity, its risk profile may be developed from one or many individual risk assessments.
When developing the risk profile:
- assess risk with both a short and long-term focus (his enables the subsequent risk profile to inform both immediate action and longer term planning),
- seek input from stakeholders and relevant subject matter experts who best understand the risks, and
- develop the risk profile in accordance with the relevant risk management framework and ensure consistent and correct use of risk terminology and categories.
Although it differs between entities, the corporate planning process will commonly link the entity’s corporate and business unit plans to its objectives. These objectives form a crucial starting point for any risk assessment in the entity, and a key focus of the entity risk profile is to manage the uncertainty around their achievement.
Just as individual risks are analysed to fully understand them, the risk profile can be analysed to identify key, common or systemic issues between and amongst the risks. Understanding these can focus attention on where the most effective change can be made.
Examples of patterns, themes and issues to look for include:
- patterns in the difference between inherent vs residual risk (the extent and consistency of difference will give an indication of the effectiveness of the entity’s control framework),
- common causal factors, where a small number of contributing issues are relevant to a larger number of risks (these may suggest priority opportunities for treatment),
- linkages between risks in different profiles (this can help understand interdependencies, relationships and the opportunity for cascading failures), and
- concentrations of severe risk in certain categories may indicate areas of particular vulnerability for review (for example, if an otherwise robust entity is managing a number of severe risks within one category it may indicate attention needs to be paid to this area).
Any risk profile needs continual maintenance. In part, this determines if there have been any changes to the risk profile caused by changes to the internal or external context. Reviewing the risk profile can assist in ensuring that:
- assumptions about risks remain valid and the external and internal context in which the risks were assessed remain valid,
- results of risk assessment are in line with actual experience,
- risk controls are being maintained and assured, and that proposed treatments are being implemented as required, and
- assumptions around the interrelationships and linkages between risks at all levels at the entity and the impact of change in one risk on another, remains valid.
The monitoring and reporting cycles of corporate plans and risk profiles can be aligned to create synergies between the two activities. The monitoring and review process needs to keep pace with changing priorities and the refresh of the corporate plan is a good opportunity to refresh the relevant risk profiles in their entirety.
Practical strategies that can be used to guide the review of an entity’s risk profile include:
- Having a relevant risk owner or steward present an analysis of a small number of risks with a focus on key changes or concerns. Over time, this will result in a rolling program of review of the risk profile.
- Avoid the practice of reviewing every risk in a risk profile in a single meeting or session. Doing so can lead to compliance behaviours and skipping over the risks that require the most attention.
- Periodically recreate the risk profile from a ‘clean sheet’. Occasionally starting from scratch and performing a fresh risk assessment and then reconciling the results with the existing profile is a great way to ensure you don’t become fixated on simply refining existing risks.
- Establish escalation mechanisms to ensure that risks in the entity risk profile are being managed at the right level.
- Ensure those responsible for designing or implementing new policies or programs first review relevant elements of the risk profile to ensure that they understand whether risks will be created or modified and that control strategies remain appropriate and effective.
- Consider risk monitoring information already available such as audit reports, quality assurance activities, and the results of key performance indicators.
Ensure that the risk profile is communicated to the right people at the right time in an appropriate format. Some considerations when communicating the risk profile include:
- seeking feedback from executive reviewers and stakeholders on how often and to whom risks are to be reported,
- establishing well understood risk escalation and aggregation protocols so that unacceptable risks can be quickly conveyed to the appropriate level of management and that the nature of the risk is clear,
- tailoring the presentation of the risk profile to its audience and consider their risk management maturity, and
- using colour to highlight key issues and areas of concern, or focus the audience’s attention on the risks or concerns that most warrant discussion.
For further information on risk communication refer to the Comcover Information Sheet Communicating Risk.
Example 1. Traditional Risk Register
Although they vary in scale and complexity, a simple risk register may typically contain the following elements for each risk:
- risk ID or unique identifier,
- description of the risk – its cause, the risk event, and key outcome should it be realised,
- a risk category or group or family,
- sources or causal factors relevant to the risk,
- the likelihood of the risk occurring,
- the potential consequence should the risk be realised,
- control measures currently in place and an assessment of their effectiveness,
- an assessment of how the risk is changing or trending and how quickly it could be realised,
- an assessment of risk tolerability, or how the risk compares to relevant elements of the entity’s risk appetite,
- treatments (proposed controls) to be implemented to improve the management of the risk, if required, and
- owner or steward of the risk.
The table below is an illustrative example of a simple risk register.

Example 2. Risk Severity Matrix or Heat Map
A risk ‘heat map’4 or risk severity matrix plots the risks in a risk profile on a matrix or graph, with the scale of consequence on one axis and likelihood on the other. Colours and banded levels are often used to highlight risks of differing severities.
An example of a simple risk profile represented as a heat map is illustrated below. Each numbered circle refers to an individual risk. The structure of the heat map and the severity levels will be defined in the entity’s risk management framework and should reflect the considered risk appetite of the entity.

Example 3. Inherent risk severity vs control effectiveness
Other representations of a risk profile may seek to communicate a particular message, concern or pattern.
The example illustrated below plots the control effectiveness rating of the risk on one axis and the inherent risk severity on the other. Again, each numbered circle refers to a risk in the risk profile.
This particular representation shows whether risk control strategies are effective in managing the entity’s risks, and where further investment may be needed. It helps differentiate those risks which are inherently low and those which are only low because of a high degree of control effectiveness (control critical risks).

Control critical risks - are inherently severe, but currently well controlled. They may represent a low level of residual risk but only because of the effectiveness of current controls. These risks require active monitoring and management and an assurance strategy to ensure the risks do not increase in severity.
Insufficiently controlled risks – are inherently severe and are assessed as being inadequately controlled. They may represent high residual risks. Insufficiently controlled risks likely require additional treatment.
Inherently low risks - require active monitoring to ensure that any changes in the internal and external context do not make the risk more severe.
Potentially over controlled risks - are inherently mild with high levels of control. These risks need to be monitored to ensure they do not become more severe over time, but also represent potential opportunities for efficiency gains if redundant or excessive controls are found.
Example 4. Risk exposure compared to risk appetite
It can be useful to explicitly compare the level of risk exposure represented in a risk profile against the risk appetite of the entity. This helps decision makers understand if they are carrying too much, too little, or just enough risk. This can occur at an individual risk, risk category, or whole of profile level.
In the conceptual example illustrated below, the entity’s risk profile (or exposure) represented in red is outside the most desirable risk tolerance band. Action may need to be taken to reduce the risk, particularly if the risk assessment suggests the risk is likely to rise further.

The manner in which this is represented in practice will vary depending upon how the entity articulates its risk appetite and the target audience. Illustrated below is a simple table that presents a risk profile of six risks, comparing the current exposure against the risk tolerance for that category of risk. The rightmost column clearly illustrates to a senior decision maker where risk is above, below or in line with the relevant tolerance and the direction the risk needs to be driven.

The aim of this information sheet is to assist Commonwealth officials at the Specialist and Executive levels. It outlines the:
- benefits of developing of an enterprise critical risk register;
- process and practical tips to establish an enterprise critical risk register; and
- importance of obtaining Senior Executive Service (SES) officer endorsement and involvement in the development of and enterprise critical risk register.
This information sheet provides guidance and a framework for entities seeking to develop a critical risk register at an enterprise level.
Benefits of developing a critical risk register include:
- alignment of a risk profile to entity strategies and group level objectives
- more use of risk management controls in business planning discussions
- achievement of corporate objectives
- more emphasis on risk-based judgements as part of decision making processes, for matters such as priority setting, resource allocation and performance measures
- increased understanding of critical enterprise risks in connection to business group risks.
An enterprise critical risk register is an entity wide view of significant risks (as mapped against the corporate plan priorities and objectives), as well as critical, common and shared risks.
There are four key elements needed for developing and maintaining an enterprise critical risk register:
- Entities should construct a risk toolkit such as a framework with guidance on the risk management process to frame the discussion when developing the Register of risks.
- Entities should develop a communication campaign. The campaign should target the people to be involved with developing the Register, and focus on raising awareness of the framework and the organisational benefits of enterprise risk management. The campaign should also outline the process of developing the register.
- A risk working group should be established to report results to SES and periodically update the Register.
- Having a Deputy Secretary as a sponsor for the work to raise awareness of it and encourage participation in workshops.
The Establishment of an enterprise critical risk register can include the following steps. However as operating environments and the objectives of each entity are different, the below framework should be adjusted to fit specific needs:
Preparation stage
Implement the communication campaign by:
- Engaging with each business group SES to confirm attendance at a pre-workshop. Explain the workshop will establish objectives to manage each business group’s strategic risk priorities and how it will feed into the enterprise critical risk register.
- Identify and liaise with select non-SES staff that will attend the workshops and communicate what an enterprise critical risk register is, the process to develop it, and the role they will play (providing an operational perspective) at the workshops.
- Develop a pre-workshop information pack. This includes an agenda outlining workshop activities, pre-reading, and timeframes and intended outcomes.
- Distribute the information pack to participants prior to the workshop to raise awareness of risk terminology and the entity’s risk framework.
- Contact workshop participants and advise them to compile a list of business objectives and statements to be prepared and brought to the workshop. These should describe, “what must go right” statements (WMGRS), in order to achieve particular objectives linked to the strategic priorities.
Workshops stage
Ideally, workshops should have 12–15 people including SES, risk working group representatives, a facilitator and subject matter experts. Each workshop can be structured as follows:
- The workshop begins with a discussion raising key business group objectives and critical priorities, with a Deputy Secretary (the sponsor) to set the context for the conversation (approximately 15 minutes).
- There is then a brainstorming session that requires participants to identify their views on post-its about the WMGRS to achieve the business group’s objectives that were prepared prior to the workshop. This involves discussing the drivers to achieving the WMGRS and documenting the uncertainties that could jeopardise the achievement of those drivers – these uncertainties can affect each business group’s objectives and critical priorities (approximately 30 minutes).
- The facilitator then groups the post-its containing the uncertainties for each WMGRS in common themes on the whiteboard. Risk events are then distilled into broad risk statements comprising of the source, risk and consequence (approximately 90 minutes).
- The group then discusses how to record and prioritise these risks (approximately 5 minutes).
- There is then a discussion to agree post-workshop timeframes and activities (approximately 10 minutes).
Outcome – Output phase
Information from the workshop will be used to develop an enterprise critical risk register. The process used to create the register is outlined below.
- Each risk identified at the workshop is assessed and recorded in the Register. It is important to accurately record the risks, their sources, consequences, controls and ratings to help with ongoing monitoring and review of the Register.
- Once all risks are compiled by a risk working group representative, a risk owner is then agreed upon for each risk. The owner has overall accountability of the risk and is responsible keeping an eye on the internal external environments to ensure the risk remains relevant, works with control owners to manage the risk within the agreed tolerance, and manages the update of the Register with the Working Group as necessary.
- Much like risk owners are agreed upon, control owners are also agreed upon. The control owners have overall accountability in implementing, managing and monitoring the controls to manage the risk. All control owners should work in coordination with each other to ensure their respective control activities are not duplicating or compromising the activities of other control owners.
- Once all the relevant information has been recorded to develop the Register, it is then validated and signed off by the Deputy Secretaries and reviewed and discussed on an ongoing basis at Executive Board meetings.
Following establishment, the register can be utilised to undertake the following:
- Establish a statement of the entity’s risk profile in order to achieve entity objectives.
- Enhanced risk based decision making to assist with the design and delivery policy and programs.
- Inform the corporate planning process and priority setting.
- Facilitate reporting to the Executive, risk audit committees and other stakeholders on key risk themes, exposures, opportunities and activities.
- Design training programs to better equip staff to interact with common and shared risks.
SES engagement
- Deputy Secretary engagement and SES involvement is important to demonstrate the importance of the Register, and to instill a shared understanding around risk in the entity. A Deputy Secretary sponsor can be useful is raising awareness and participation in the workshops.
Planning
- Dedicated brainstorming sessions and workshops provide directed discussion. They also provide a means to align leadership perspectives with entity risk priorities.
- Ensuring the right people are in the brainstorming sessions is essential to form perspective in the development of the register. This also helps to ensure relevant discussions around entity risk at the operational level, with focus on alignment to strategic business priorities.
Collaboration
- Coordination with the Risk Working Group representatives facilitates proper functioning of risk management in alignment with the Register.
- It is critical to agree on risk and control ownership during the output stage and to clearly delegate work, in order to populate risk records within reasonable timeframes.
- The Corporate Risk Team must be involved in all steps to support the process and to incorporate feedback into the development of supporting risk artefacts. It also allows them to establish relationships with risk and control owners and obtain an understanding of future training requirements.
- The creation of a risk assessment to capture risk information helps to create a shared understanding of the risk, its drivers, and possible treatments.
This information sheet is intended to assist all Commonwealth officials. It outlines the core elements of how to facilitate a risk workshop.
A risk assessment or risk workshop is a useful activity to identify and discuss the management of risks for projects or programs. They allow for different viewpoints from stakeholders and subject matter experts to be heard and for the relative criticality of risks to be established. The practical tips outlined in this information sheet aren’t exhaustive, and some may seem obvious, but they provide considerations that can contribute to the success of a risk workshop.
A risk workshop allows a project team to work together to identify risks for a particular project or program, which can be referred back to over the course of project’s development. Holding a risk workshop in the planning stage of a project means you and your team are aware of any risks that may impact your objectives. It may also inform the design and development of policies.

Once completed, you should have a documented risk assessment that can be reviewed regularly as activities progress. Risk workshops are flexible and can be easily tailored to specific projects. This means they are useful for projects of any size or complexity.
Establish a clear scope
- Meet with the contact or team that requested the workshop. This is where the expectations for the workshop can be set. They may need assistance with limiting or expanding their scope.
- Define whether the workshop is for a particular team, project, process, policy or program.
- Write down and get sign off on the scope to ensure the group understands the workshop’s objective.
Ensure you have the right people in the room
- The attendees will make (or break) how successful your risk workshop will be. It is therefore important to know who the stakeholders are. Some considerations might include whether you have appropriately senior people with influence and delegation (if needed), people with the right subject matter expertise and people with appropriate experience. This includes those with involvement in similar work or projects who can play a vital role in sharing lessons learned.
- Consider whether you should invite people from other but linked teams/areas who you may share risks with.
- Stress the importance of key people attending and request that they don’t send a proxy.
- Ensure that people know why they are there and why they are important to the process. It is also important that they are aware of what type of insights they are expected to share.
Decide the workshop format
- There are many approaches to running a workshop. Consider what format will work best for your audience. A traditional workshop usually includes the identification of risks for your team/process/business/activity. These are rated and/or ranked by consequence/likelihood and control effectiveness.
Other common formats include:
- A “what must go right” approach where you decide on your objective and work backwards to identify the risks to achieving it. This is useful for most audiences and is particularly useful when considering project/program risks and strategic risks to the organisation itself.
- War games involve a group of diverse subject matter experts and stakeholders working through a plausible risk being realised to challenge their assumptions and work through how they could respond to the risk. This can be useful at the executive and strategic level to look for vulnerabilities and immediate crisis response capability (without the real life consequences).
- Pre-mortems This can take a number of forms, but it is essentially imagining that you failed to achieve your objective. Then working backwards think about what you should have done to prevent the failure and identity what went wrong. This can be a fun and effective way of trying to put back the pieces and to learn from hypothetical mistakes. This is usually most engaging at the officer level and in small teams (but with all relevant stakeholders present to prevent blind spots).
- Bow tie analysis is a visual method of understanding a risk better through analysing the preventative, detective and recovery controls with the risk event depicted in the middle (the knot in the bow tie). This is particularly useful in better understanding incidents that have occurred, for understanding risks that have not yet occurred and for developing key risk indicators to provide early warning.
Get your logistics completed early
- Book the room/facility. Consider whether it is big enough and think about the best configuration (you may want to break out into smaller groups).
- Check if you need audio visual equipment and check that it works in advance of the workshop.
- Think about whether you will need to conference call in participants.
- Send the meeting invite out well in advance to block out time in diaries. Consider a placeholder while you finalise the scope.
- Check you have enough equipment, pens, paper, flipcharts etc and decide how the discussion will be documented.
- Circulate the tools and templates to be used in the workshop as well as any additional background information.
Use the risk framework
- Ensure that you use the relevant entity’s risk framework and supporting tools and templates. For example don’t use a consequence/likelihood matrix that is separate from what the rest of the entity use (even if it is better). Using a different tool will make it extremely difficult to consolidate the findings into the entity’s framework. It will also make comparing and ranking risks from the rest of the entity impossible.
- Consider what work is best done in the workshop (such as discussion, debate and creative ideas) and what is best done outside a workshop (detailed analysis and documentation etc).
- If the risk framework has broad categories of risks, use these to stimulate conversation when identifying risks.
“Fail to prepare, prepare to fail”
- If possible obtain as much reference material about the project or subject you are undertaking the workshop on. Ideally before the workshop you should read the…(If available) Business case/project plan/implementation plan/financial plan/stakeholder management plan/communication plan.
- Know your audience. If the workshop attendees have a low risk management maturity then keep it simple and think about doing some of the thinking (to be challenged) beforehand. Consider separating the workshops and use each to consider one aspect (such as a workshop dedicated to identifying the risks, another to rate them etc).
- Run through likely key risks that may emerge during the workshop – get prior input from the key client contact, your own experience or research. If you are pressed for time, think about sending out a pre-brief with the context of the project, project outcomes and scope of the workshop.
- Consider contacting the workshop members prior to the workshop to understand and even articulate some of the key risks to save time and better focus the workshop. You could try asking participants to come to the workshop with some information on the risks that are worrying them, the risks they feel are over-managed and those they need help managing from other areas.
- Practice. Conduct a dry run with team members to practice the timing and pitch of the workshop.
- Know when to move on – have a flip chart (or similar) marked “Parking Lot” where you can note issues for further, offline, discussions.
- Have a plan for how to deal with the loudest voice in the room. Risk workshops are more robust when multiple views are heard. If someone is dominating the discussion, directly ask others for their opinions, switch the point being discussed etc.
- Consider having two facilitators. The second can be useful as a scribe and also to prompt discussion when/if separating into groups for discussion.
Be prepared to challenge
- The facilitator of the risk workshop plays a critical role as an impartial participant.
- Where participants raise points or rate risks in a way that doesn’t feel right, the facilitator should raise their thoughts for consideration.
Write up quickly
- Write up the output soon after the workshop to ensure you capture all the detail whilst still fresh in your mind.
- Send this to the key stakeholder for approval.
- Use templates that present the output in a clear and easy to understand format.
Agree and define the next steps
- Discuss and confirm the next steps before the workshop ends. Make sure this is practical so that the information generated will be used and practical.
- Discuss how to keep the outputs up to date and relevant. If possible discuss a review date and who will be responsible for coordinating the review.


